Dorothy (aka @maclurker) warns the live chatroom to behave, why I told my friend Nancy to get a Samsung, and a story of woe on trying to upgrade two old Mac so they can do shared photo streams. In Chit Chat Across the Pond Bart answer’s Leon’s dumb question about VPN security. He gave us some good diagrams of 3 VPN scenarios to answer Leon’s question. Then Bart teaches us about the theory behind the Public Key Infrastructure, or PKI, and what it means in the real world.
![]()
mp3 download
Hi this is Allison Sheridan of the NosillaCast Mac Podcast, hosted at Podfeet.com, a technology geek podcast with an EVER so slight Macintosh bias. Today is Sunday September 1, 2013 and this is show number 434. Hey you know what’s SUPER fun??? Recording a podcast with a sinus infection! Luckily for you guys I’m drugged up, and even luckier I recorded one of these segments a few weeks ago, and luckiest of all Chit Chat Across the Pond with Bart went kinda long so you don’t even have to listen to me very much. Best of all worlds I figure! Before I get started though, Dorothy has a special message she asked me to play for the live audience. Let’s here what she has to say to them.
Dorothy to the Chat Room
Hello Nosillacastaways! This is MacLurker. Well, I’m off on my travels again and will not be in the chat room for the next couple of weeks. But, in case you miss me, I thought I’d leave a brief message with Allison. Please be sure that you all are good boys and girls in my absence. No taking over all the chairs in the front row (I’m looking at you, Kevin), no spit-balls, and no laughing or heckling from the back (I’m looking at YOU, switcher mark). Don’t make me pull the boat over and come back to deal with any bad behavior. I will NOT be happy. And I will NOT be nice.
But, there. I’m sure you will all be good and that you will give Allison all the help, support, and respect that she needs. And the show will have its usual excellent form.
Thanks Dorothy – I appreciate you trying to keep the miscreants in line.
Why I Told My Friend to Get a Samsung
Everyone listening to this show is probably a pretty sophisticated computer and smart phone user, and I know many of us try to protect the norms in our lives from making poor tech decisions. This week my friend Nancy announced proudly to me that she had finally broken down and bought an iPhone. I cringed that she bought right before the new one is probably coming out but the story got so much worse I didn’t even have time for that.
After her announcement she followed up by saying she wasn’t sure she was going to keep it, that she didn’t like it very much. She said the screen was so small compared to her Galaxy S3 that she had before that. She pulls out her “new” phone…and it’s an iPhone 4!
Now for the background on how this horror occurred. She had been with T-Mobile for a long time, doing the every two year upgrade for her and her two teenage boys. When she went to talk to them recently, I think they confused her with this new plan T-Mobile introduced recently called T-Mobile Jump where you pay a monthly fee to buy the phone on top of an up front cost. She ran the math and didn’t like what she saw, and decided to dump T-Mobile and went to the Verizon store. Her sons wanted iPhones so she laid down a lot of cash. She looked at the prices and saw the free iPhone 4 and went for that, and mentioned that her sons laid out the big bucks to go with 4S’s so they’d get Siri.
I can only assume that it’s against Verizon’s policies to even mention that there just might be a new iPhone in 3 weeks, especially since it’s not a fact but just a rumor at this point, so I guess I can’t holler at them for not suggesting she wait just a few weeks before making this big commitment. What I CAN holler at them for though is that they convinced her or allowed her to buy a THREE YEAR OLD iPhone to replace a one year old Samsung Galaxy S3! What were they thinking? She got a phone that has a way way way smaller screen (even the iPhone 5 would have shocked her in it’s size), it has a way way way slower processor, AND it won’t even work on the Verizon 4G/LTE network! Why the heck would they let her do that???
The good news to this story is that I had this conversation with Nancy only about 5 days after she bought the iPhone 4, and I encouraged her to stomp back into the Verizon store and DEMAND a change. You’re not going to believe this but I told her to demand a Samsung Galaxy S3! She liked that phone, it wouldn’t cost her much since it is a year old, she’ll have all her apps and her big screen AND she’ll get access to 4G/LTE. If there were a way she could have held off till the new iPhone came out I’d have suggested that she at least give it a look, but the timing of the 2 week return policy made the Samsung the only good choice.
I still can’t believe Verizon allowed her to do something like this, they should be spanked, but at least there’s a happy ending – she did get the Galaxy S3 and she’s delighted to have it back.
Upgrading
Steve’s parents switched to the Mac from Windows 98 about 5 years ago. They bought a white MacBook and a 21 inch iMac. They love their Macs. They started with Leopard, and a few years back I upgraded them to Snow Leopard. Steve’s mom, Merlee, loves to learn new stuff on the Mac, Steve’s dad, Ken, finds change abhorrent.
So what to do when Bart told us that Snow Leopard was no longer being supported by Apple? Procrastinate, of course! I put it on my to do list to tell them they needed to upgrade. I put it on my to do list to go to San Diego to do it for them. I put it on my to do list to buy them Mountain Lion. But I didn’t actually DO it. While it would be great entertainment to explain “natural scrolling” to Ken, it would take about 3 days of my life. And then Apple started doing a smattering of security updates to Snow Leopard from time to time so my procrastination was rewarded! Plus moving them off of Snow Leopard meant upgrading their version of Office – and explaining the ribbon to Ken was something that I wanted to avoid as long as possible.
But then we went on our vacation together, and I created a shared photostream of each day of the trip, and realized that Merlee couldn’t join them because her version of iPhoto was so old. She was running iPhoto 6! While on vacation I showed Office 11 to Ken and Merlee – and they both said they didn’t think it would be all that bad! On the home tab they could see pretty much every function they cared about, so they said “let’s upgrade!”
So I had 3 tasks – upgrade the OS, upgrade Office, and upgrade iPhoto. We drove to San Diego to do the upgrades. But then Merlee and I decided o go for a long walk instead. And then we decided to make vodka lemonades…
 So the NEXT day bright and early I got up to start the upgrades. Let’s get an early win by starting with iPhoto 9. Nope. Even though in Snow Leopard she has the app store, it says she can’t upgrade to iPhoto 9 without upgrading her OS. Ok fine, we’ll get Mountain Lion. Nope. Mountain Lion won’t run on a late 2008 White MacBook. Oh well, we’ll go to Lion then, right? Nope. Can’t buy Lion in the app store. I remember this being a problem but the solution was to go to an Apple store and say the secret words and they’d stealthily hand you a Lion disk under the table. Since I’d wasted the previous day drinking vodka lemonades (they’re delicious by the way), I didn’t have tome to go gallivanting around town to an Apple Store. One thing about being retired, you actually reach for the phone more often because you actually have time for that kind of thing. I called Apple and the guy had a GREAT solution! turns out you can buy Lion from Amazon for $25, they email you a code, and you use the Redeem feature in the Mac App Store to buy Lion. Pretty cool solution I thought. Great – we did that and installed Lion without a hitch.
So the NEXT day bright and early I got up to start the upgrades. Let’s get an early win by starting with iPhoto 9. Nope. Even though in Snow Leopard she has the app store, it says she can’t upgrade to iPhoto 9 without upgrading her OS. Ok fine, we’ll get Mountain Lion. Nope. Mountain Lion won’t run on a late 2008 White MacBook. Oh well, we’ll go to Lion then, right? Nope. Can’t buy Lion in the app store. I remember this being a problem but the solution was to go to an Apple store and say the secret words and they’d stealthily hand you a Lion disk under the table. Since I’d wasted the previous day drinking vodka lemonades (they’re delicious by the way), I didn’t have tome to go gallivanting around town to an Apple Store. One thing about being retired, you actually reach for the phone more often because you actually have time for that kind of thing. I called Apple and the guy had a GREAT solution! turns out you can buy Lion from Amazon for $25, they email you a code, and you use the Redeem feature in the Mac App Store to buy Lion. Pretty cool solution I thought. Great – we did that and installed Lion without a hitch.
Back to the Mac App Store to buy iPhoto 9, easy peasy for a mere $15. Install and guess what? You can’t do shared PhotoStreams in Lion! ARGH! I’ve now cost her $40 so far and she can’t do the MAIN thing she wanted to do. I was so mad! why the heck would the OS (only 1 rev behind) affect whether the CURRENT version of iPhoto could do shared PhotoStreams??? Sigh.
Well now that I can’t achieve my main objective, I HAVE to upgrade her Office to 2011 since her old version won’t even run on Lion. Remember me bellyaching to Chris Ashley of the SMR Podcast about the new pricing on Office? It used to be $149 for Home and Student which gave you 3 licenses for 3 Macs. Now it’s $139 for EACH Mac. It will cost hem $280 for a 2 year old version of the software, or I could put them on Office 365 that would cost them $100 a year for 5 Macs. They didn’t seem interested in the lease model, so I decided to buy (while swearing under my breath at Microsoft).
Now where to buy? I called the Apple to see if they had it in stock and while they said yes, they said it’s just a code in the box so no advantage to driving over. I could buy from Staples, Apple or even Microsoft themselves and it would be a download. I started at apple.com/store but the site implied (or I inferred) that they were going to ship the dumb box with the code in it instead of emailing me the code. I decided not to go to Microsoft.com because I wanted someone else to get a cut of their money at least. I went to Staples.com in the end because it clearly said DOWNLOAD in the description. Got Merlee to let me spend even more of her money and bought one license of Office for her online. We waited and waited and waited for the email, took about 20 minutes, and when we got it, it showed an expected delivery date for the box in 3 days! you’ve GOT to be kidding me! I picked up the phone again (remember, retired people use the phone) and started to let the woman who answered have it with both barrels, when she said, “that email is SO misleading. You’ll get another email in a few minutes with the code. Sorry it’s lame!” I loved her.
Few minutes later, and we get the codes, do the download and run the install. Yay! Looks like ONE thing when well and I’d still have time to play with her to show her how Office 2011 works. I launched it and it asked whether I wanted it to automatically check for software updates. Why yes I would thank you. And it found a critical update. SERIOUSLY Microsoft? I JUST downloaded it from you!!! Argh. Run the update. FINE. Updater checks again, and there’s ANOTHER update! I couldn’t believe it! Eventually it stopped this nonsense and I was able to hand Merlee her laptop, point at Office and say “good luck!” as I ran out the door. Get this. She sent me a thank you note later about how wonderful what I did was for her. I spent $179 and she’s got a new version of Office she didn’t need.
Now it’s time to turn to Ken’s machine. It’s a bit younger, so could probably go to Mountain Lion but if he and Merlee are on different OS versions you know it will be a nightmare. We were running short on time but I thought I’d give it a shot. Remembering that the installer file disappears when you’re done, I was smart enough to copy the Lion installer file from Merlee’s machine to Ken’s on their local network BEFORE installing Lion on Merlee’s machine. Ok, let’s go! Nope. Ken’s machine has 1GB of RAM in it and you need 2GB. Sigh. Normally this would be no big deal, upgrading to 2 or even a whopping 4GB is a matter of emptying out the change from the couch but that would mean waiting for it to be delivered in a few days. We searched everywhere locally for about an hour and came up empty – because the RAM required was so old. So…Ken doesn’t get Lion and he doesn’t get the new Office, at least not until the next time we go down to visit.
There’s a moral to this story. People think I’m nuts for buying my Macs on day one and upgrading apps and OSs on day one because I suffer through the bleeding edge syndrome. The first Titanium MacBook Pro was a mess, the first aluminum MacBook Pro had to have 2 logic boards replaced in the first 3 months, and you’ve heard endless tales of OS and app problems. HOWEVER, I contest that the problems for those who resist upgrading till the last minute have at least as many problems. I still get emails from people asking if I can help them import their Claris Works documents to Word, or get their contacts and calendar out of the Palm Desktop. I think the sweet spot might be say 3 months after something new comes out. Hardware and software bugs have been discovered and worked out but nothing is old and cruddy now.
Clarify
Last week I was helping my friend Doreen with a few problems she ran into moving from her iPhone 4 to her new iPhone 5. I was able to merge her contacts with her Mac (somehow when Apple did it they got phone numbers but not physical addresses) but her real joy was when I got her ringtone back (Footloose) – that’s when she actually danced around the room. After an hour and a half chatting and working I ran out of time, and THEN she asked me how to sync photos from her iPhoto (taken on a real camera) back over to her iPhone. She’s got the current version of iTunes (11) but she’s on Snow Leopard so she can’t do any kind of iCloud syncing or anything like that and I actually don’t use iPhoto, so I was at a loss. I ran out of time but promised I’d ask Twitter how to do it.
That night I threw the question on Twitter, and both @Starmike and @Philip_From_AU jumped in to help. I have to give Starmike chops for sending me the official Apple support article on it (which I’d been unable to find using the Googles). I liked what Philip from Australia did even better, he sent me a link to a Clarify document he whipped up for her. It turns out it’s pretty simple, you plug in the iPhone, open up iTunes, tap on the Photos tab and then click the Sync Photos from checkbox. Without Philips Clarify tutorial though, I’m 100% certain she wouldn’t have even tried to tackle it. He took two screenshots of iTunes with his iPhone plugged in, dropped in some annotation bubbles and a couple of arrows on each shot, and he was done. It was super simple for him to teach Doreen – literally half a world away – with the help of Clarify from BlueMango Learning. If you know stuff, and like to help other people learn stuff, and like to have them only ask you ONCE, consider buying Clarify from clarify-it.com. Cross platform version, or App Store Version, it’s all good!
Chit Chat Across the Pond
Security Light
Important Security Updates:
- LastPass patch bug that could leak passwords – http://nakedsecurity.sophos.com/2013/08/18/lastpass-password-manager-gets-security-patch-against-password-leakage-bug/
Important Security News:
- Overblown security news story of the week – passwords are not dead! The fact that Hashcat can now work on passwords longer than 15 chars does not mean the sky is falling! Similarly, the fact that password crackers are now using words as letters and looking for passwords made of a sequence of words is also not the end of the world – the answer is to pad your words with random digits and symbols (XKPasswd did this from the start because I always expected that people would start to use dictionaries in this way) – http://arstechnica.com/security/2013/08/thereisnofatebutwhatwemake-turbo-charged-cracking-comes-to-long-passwords/
- Another OS X text rendering bug causes a DOS on OS X and iOS – big problem is that when an app crashes it will try to re-open it’s last state, re-display the problem text, and crash again! Solution is to hold down shift on launch on OS X – http://arstechnica.com/apple/2013/08/rendering-bug-crashes-os-x-and-ios-apps-with-string-of-arabic-characters/
- Apple block out-of-date Java on OS X for this third time this year – if your Java is not working, upgrade to the latest version and it will work again – http://www.macobserver.com/tmo/article/apple-blocks-mac-java-plug-ins-over-security-threats-yet-again
Suggested Reading:
- The sudo bug we talked about a few months ago and which Apple have STILL not patched has now been added to metasploit – perhaps now Apple will FINALLY patch sudo? – http://arstechnica.com/security/2013/08/unpatched-mac-bug-gives-attackers-super-user-status-by-going-back-in-time/
- Poor source-checking of URLs causes security problems for iOS and Android apps – ultimately apps should only obey URL requests from trusted sources, and that’s the programer’s responsibility, but, the iOS and Android APIs could (and arguably should) make this easier for developers to do – http://arstechnica.com/security/2013/08/ios-and-android-weaknesses-allow-stealthy-pilfering-of-website-credentials/
- Facebook releases first report on Information Requests from Governments – http://nakedsecurity.sophos.com/2013/08/28/first-facebook-government-requests-report/
- US government finds that 79% of mobile malware affects Android, but only 0.7% affects iOS – http://www.tuaw.com/2013/08/26/u-s-government-finds-0-7-of-all-mobile-malware-affects-ios-wh/
- German Government deems Windows 8 too ‘dangerous’ to use (Windows 7 is OK though) – http://bgr.com/2013/08/21/microsoft-windows-8-nsa-back-door/
- Microsoft warn users just how insecure Windows XP will be when support ends next April – http://nakedsecurity.sophos.com/2013/08/19/microsoft-predicts-bleak-future-for-xp-users-after-patches-run-out/
Dumb Q:
I think a picture says a thousand words, so I’d drawn some diagrams to illustrate what is safe and what is not. When looking at these diagrams, remember that traffic flows in both ways between the VPN client and the VPN server. The traffic is ONLY protected between the client and the server, and NOT between the server and the final destination. If both the server and the destination are within the same trusted network, all is well.
Click Here for high res PDF of Bart’s Diagrams
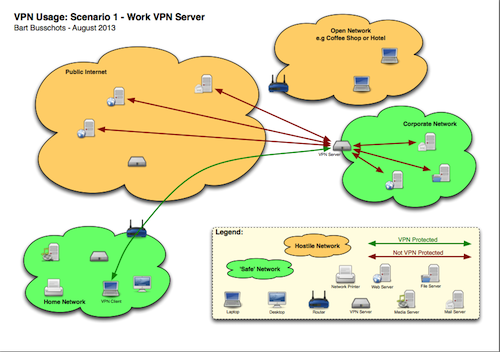
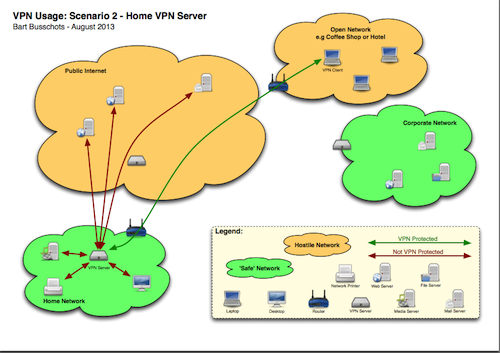
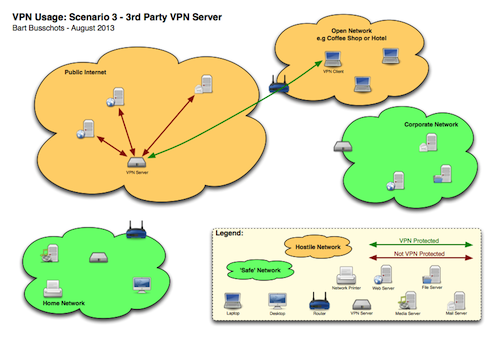
Looking at the diagrams, green traffic is always fine, no matter whether it is on a hostile or a safe network. Red traffic is fine as long as it is in a green network. The danger point is when you have red traffic in a red network.
Bearing all that in mind, lets look at scenario 1, you are using a VPN to conned to your work network. In this case, it is safe to use the VPN to access servers within your corporate network, but the VPN provides NO PROTECTION when accessing servers on the public internet through the VPN.
Scenario 2 is connecting to a VPN server within your home network from a hostile network (coffee shop, hotel, etc.). In this case the VPN provides protection within the hostile network, and gets your traffic safely to your home network, where you can safely connect to your media servers or what not. If you use this VPN to connect to servers on the public internet the VPN will protect this traffic as it passes through the hostile network, but not as it passes from your house to the public internet.
Scenario 3 is using a 3rd party VPN provider and connecting from a hostile network. Here, your ONLY protection is between your laptop and the VPN server on the internet, all traffic will exit that server to continue it;s journey un-protected. This means that the ONLY problem solved here is that the VPN gets you safely out of the hostile network you are in.
The most important thing to note in ALL these scenarios is that NO VPN REPLACES HTTPS. In all cases, the VPN failed to provide protection all the way between you and the server on the public internet. Whether or not you use a VPN, if you are sending sensitive data to or from a server on the internet, you MUST use HTTPS/SSL/TLS/SMIME to be safe.
P.S.
If people are wondering where I got the cute icons for the diagrams – this is where: http://www.opensecurityarchitecture.org/cms/library/icon-library
Main Topic – Understanding the PKI (Public Key Infrastructure)
PKI stands for Public Key Infrastructure, and it describes the architecture that underpins much of our online security, enabling technologies like HTTPS SSL/TLS, VPNs, S/MIME, and enterprise WiFi among other things.
What problem(s) does the PKI solve?
Formally:
- Authenticity – we can be confident that something which has been authenticated using a PKI certificate really does come from the source it claims to.
- Integrity – we can be confident that communications signed using a PKI certificate have not been altered since they were signed.
- Confidentiality (optional) – If a PKI certificate is used to encrypt some form of communication we can be confident that no one eves-dropping on the communication can decrypt it.
What does that mean in the real world?
- Authenticity: when we connect to a website over HTTPS we can be confident we really are talking to the server we think we are talking to. When connecting to a VPN we can be confident we really are connecting to the VPN server we think we are connecting to. When connecting to a corporate-style wireless network (the enterprise version of WPA not the home version) we can be confident we really are connecting to the network we think we are connecting to, and not just an AP with the same SSID as the network we want. When we receive an S/MIME signed email we can be confident it really came from the address it claims to come from.
- Integrity: when we visit a website over HTTPS we can be confident that the HTML arriving in our browser is exactly the same HTML that was sent by the server – i.e. that no one has inserted or removed any code. We can also be confident that traffic being sent through a VPN tunnel will emerge un-altered at the other side. And, when we receive an S/MIME signed email we can be confident that the email we receive is exactly the email that was sent.
- Confidentiality: When we browse to a HTTPS website we can be confident that no one in a position to eves drop (the bank’s ISP, our ISP, the corporations that run the internet backbone, our fellow coffee drinkers at SBUX, our colleagues on a work LAN, our family on a home LAN, or our fellow guests on a hotel network) can see our banking details or our FaceBook cookie or anything else being sent over HTTPS. We can be confident that S/MIME encrypted email cannot be read by anyone in a position to eves drop, or, anyone who has access to our mail while it rests on a server. It also means that we can be confident that no one can see into our VPN tunnels.
How does the PKI Work?
The PKI promises a lot, but surprisingly, at it’s very heart are just two relatively simple principles. I consider these to be the two atoms of the PKI, with the PKI as a whole being made out of molecules assembled from these atoms.
Atom 1 – Message Digests (AKA Hashes)
A message digest is a fixed-lenth checksum generated from an arbitrary length input. Good message digests are very sensitive to changes in input (i.e. a small changed in the message being digested will result in a large change in the digest). Digests need to be easy to generate but hard to reverse (i.e. it should be really hard to tweak a message to force it to arrive at a pre-determined digest). A really easy way to get a good message digest is to use a cryptographic hashing function like SHA256 (in the past MD5 and SHA1 were used extensively).
The function of a message digest within the PKI is to detect changes, not to encrypt or hide information, so while the technology is very similar to password hashes, the application is very different. The biggest difference is that when it comes to PKI, salting makes no sense, while when it comes to password protection, it’s not salting that’s senseless!
e.g. you can play with message digests using the Terminal on your Mac:
cc-dsk-2ss:~ bart$ echo ‘monkey’ | md5
2f548f61bd37f628077e552ae1537be2
cc-dsk-2ss:~ bart$ echo ‘Monkey’ | md5
c2271272a52341872d521a4e2b40172b
cc-dsk-2ss:~ bart$
Notice that just changing the m to an M has totally changed the digest.
Atom 2 – Asymmetric Encryption
Most people when they think of encryption think of using a password to protect something. The same password is used to encrypt and decrypt. This is so-called symmetric encryption. There is another kind of encryption where, rather than a password, there is a pair of keys. What ever you encrypt with one key can ONLY be decrypted with the other. Both keys can be used for encryption.
Molecule 1 – Public & Private Keys
At the instant you generate an asymmetric key pair there is no real difference between the keys. However, within the PKI we introduce the concept that one of the two keys must be chosen to ALWAYS be kept secret, and the other to made public. Which of the two you choose is totally arbitrary, but once you choose there is no going back. Sharing the public key in no way compromises your security, in fact, you HAVE to share your public key for the PKI to function. The private key on the other hand MUST remain private, the instant you lose control of it, you lose your security.
Molecule 2 – Digital Signatures
Because of the nature of asymmetric encryption we know that if something can be decrypted with your public key then it MUST have been encrypted with your private key, and, assuming you have not lost your private key, we know you MUST have been the one to encrypt the information.
We also know that if a message is altered it’s digest will change.
Putting these two pieces of information together we can construct a digital signature that allows the recipient to cryptographically verify the authenticity and integrity of a message.
Start by creating a digest of the message to be signed. Then encrypt that digest with your PRIVATE key, and attack the encrypted digest to the message.
The recipient can then verify that you really did send the message exactly as it was received by detaching the encrypted digest, decrypting it with your public key, re-calculating the digest on the message you received and comparing the values. If the two digests do not match the message is in some way fake – either it’s not really from the who it claims to be from, or the contents has been altered.
For practical reasons – when things are digitally signed in the real world, what gets attached to the signed message is the encrypted digest AND the certificate of the person who is claiming to be the source. These three pieces of information are combined into a specially formatted file which we call a digital signature, often with the file extension .p7s.
Molecule 3 – Certificates
A certificate is a notarised public key – it provides a verifiable mechanism for distributing public keys, and tying those keys to some kind of identity (usually a domain name or an email address).
A certificate, like a digital signature is a specially formatted file that contains a number of pieces of information that together form the certificate.
Digital certificates contain four things:
- the public key that is being notarised
- the identity that the key is to be associated with (i.e. a domain name or an email address)
- some metadata including the dates between which the certificate is to be considered valid, and the cryptographic algorithms that should be used to validate the signature
- A digital signature or all this information from a Certificate Authority – i.e. all the above data is digitally signed by a trusted third party
Molecule 4 – Certificate Authorities
The final piece ingredient in the PKI is the concept of a trusted third party who can notarise all the certificates in use. There are a few hundred organisations trusted with this important task, and we call those organisations Certificate Authorities. Their private keys are used to sign certificates, and, crucially, their public keys are pre-installed on all modern operating system.
It’s that fact that every computer has a set of known-good public keys that allows the whole system to work. These known-good public keys act as the trust anchor that can be used to validate every certificate used within the PKI.
I don’t know about you guys but every time I listen to Bart talk about security I get just a little bit smarter. I think if I look back a year ago I’m a LOT smarter about it by now!
That’s going to wind this up for this week, many thanks to our sponsor for helping to pay the bills, Blue Mango Learning at bluemangolearning.com makers of ScreenSteps and Clarify. Don’t forget to send in your Dumb Questions, comments and suggestions by emailing me at allison@podfeet.com, follow me on twitter and app.net @podfeet. Check out the NosillaCast Google Plus Community too – lots of fun over there! If you want to join in the fun of the live show, head on over to podfeet.com/live on Sunday nights at 5pm Pacific Time and join the friendly and enthusiastic NosillaCastaways. Thanks for listening, and stay subscribed.
