Live show will be on Saturday at 3pm Pacific Time on 25 July as I’ll be on vacation on Sunday. There will be no live show on Sunday 2 July. I was on the SMR Podcast on Episode #262 entitled Little Community and the Daily Tech News Show Episode 2538 entitled Amazon is Past Its Prime Day this week. Learn how I lost all my Apple Watch activity data but that it was because Apple really does protect our private data. I’ve started teaching a young boy a bit about electricity and magnetism and it’s making a difference to him and his mom. Bart joins us but JUST to talk security. He tells about the hackers getting hacked this week, gives us some Security Lite and Important Security News. Then for Chit Chat Across the Pond we’re be joined by Serenity Caldwell from imore.com.
Hi this is Allison Sheridan of the NosillaCast Mac Podcast, hosted at Podfeet.com, a technology geek podcast with an EVER so slight Macintosh bias. Today is Sunday July 19, 2015 and this is show number 532. This week’s show is going to be formatted a little bit differently. I’ve got a couple of stories for you, then Bart is going to join us but JUST to talk security with us. He’s going to talk about the hackers getting hacked this week, give us some Security Lite and Important Security News. Then for Chit Chat Across the Pond we’ll be joined by Serenity Caldwell from iMore. Next week Bart will be back to join us along with Steve Sheridan for a special episode of Chit Chat Across the Pond.
Before I forget, next week’s live show will be on SATURDAY, not Sunday at 3pm Pacific Time. I’m going on vacation for a week (I know, “what’s vacation when you’re retired?” And “didn’t you just get back from India?”) so I wont’ be around on Sunday. Allister Jenks will be doing the show that will air the weekend of August 2nd so there will be NO live show on August 2nd. If you’ve been meaning to do a recording for the show, dust off that microphone and send it in! You can send them to me and I’ll forward them on to Allister for inclusion in the show. If you buy the NosillaCast App, you will get notifications of these changes!
Before we get started I wanted to tell you about a couple of shows I was on this week. First I was on the SMR Podcast on Episode #262 entitled Little Community. Robb was out so I joined Rod Simmons and Chris Ashley and we had such a blast! If you haven’t heard the show before go check it out, what a great geek time. On Thursday I was on the Daily Tech News Show Episode 2538 entitled Amazon is Past Its Prime Day. Tom and I talked about whether the desktop Office suite is dead, go check it out. Ok, now let’s jump into the show!
Blog Posts
Apple Really Does Protect Your Health Data
I Wonder What Would Happen If…
Clarify
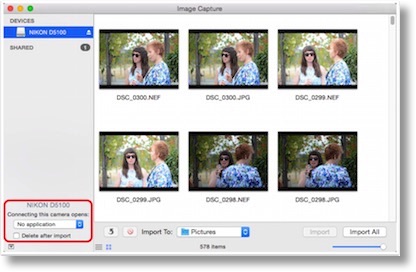 I’m a member of a local user group in town but I don’t attend the meetings. I do like to read people’s questions that they send in email though mostly because I just enjoy the heck out of knowing the answer to a problem and helping someone along the way. This week a gentleman named Michael was complaining about Apple Photos and how he HAD to use it and how he couldn’t use iPhoto any more. I explained in one response that iPhoto is still there and you can still use it. He explained back that his workflow has been stolen by Photos though because Photos keeps opening. I suspected the problem was that his default setting was to open Photos when inserting his memory card, camera, or phone. I explained that simply changing the behavior in Image Capture would fix his problem. He wrote back that it didn’t work.
I’m a member of a local user group in town but I don’t attend the meetings. I do like to read people’s questions that they send in email though mostly because I just enjoy the heck out of knowing the answer to a problem and helping someone along the way. This week a gentleman named Michael was complaining about Apple Photos and how he HAD to use it and how he couldn’t use iPhoto any more. I explained in one response that iPhoto is still there and you can still use it. He explained back that his workflow has been stolen by Photos though because Photos keeps opening. I suspected the problem was that his default setting was to open Photos when inserting his memory card, camera, or phone. I explained that simply changing the behavior in Image Capture would fix his problem. He wrote back that it didn’t work.
I finally did what I should have done in the first place. I whipped open Clarify, inserted a memory card, opened Image Capture, took 3 screenshots, put an arrow pointing to the upwards-facing teeny tiny disclosure triangle that lets you see the control of what happens when you insert a device, and showed him that you could indeed still choose iPhoto to open. I put a couple of words in to explain that you do have to insert the device to be able to get access to these controls.
This wasn’t a masterpiece I really needed to post online so I simply went to Edit and chose Copy Document to Clipboard and chose Text and Images, and then pasted it into the email and hit send. This took far less time than I’d spent with Michael going back and forth in words! I wanted to read to you what he wrote back:
Ahhhhh, Thank you Allison : ) Yes I did try the Image Capture thing in response to your first email, but I *think* I may have not had the SD card plugged in at the time, and perhaps it sets the options per device? Either way, your illustrations were perfect THANK YOU. How wonderfully kind of you, your patience penetrated my frustration, you’re awesome. Have I said thank you enough? Just in case: THANK YOU AGAIN!
If that isn’t a good enough testimonial, I don’t know what will get you to go over the clarify-it.com and download the free trial for Mac or Windows or both.
Security With Bart
Security Medium – When the Hackers get Hacked
An Italian security company called Hacking Team were themselves hacked, and 400GB of data exfiltrated. It takes time to analyse that much data, so there has been a steady stream of revelations since the new of the hack broke on the 6th of July, and that stream is still on-going.
Because this is a story that is likely to run and run, Ars Technica have created a “series” for the story on their site – basically, a single page where they continue to list all their stories related to the hack – http://arstechnica.com/series/hackingteamhacked/
Practical Consequences of the Hack – VULNERABILITIES!
So far, four zero-days have been found in the leaked data:
- Three separate Flash Zero-days, all now patched by Adobe – http://arstechnica.com/security/2015/07/adobe-flash-exploit-that-was-leaked-by-hacking-team-goes-wild-patch-now/ & http://arstechnica.com/security/2015/07/once-again-adobe-releases-emergency-flash-patch-for-hacking-team-0-days/
- An IE11 Zero-day, now patched by MS – http://arstechnica.com/security/2015/07/ms-kills-critical-ie-11-bug-after-exploit-was-shopped-to-hacking-team/
All these Flash problems, hot on the heals of other Flash problems, have had an effect on the IT community as a whole, and re-invigorated the debate on Flash.
Software makers like Apple and FireFox again blocked vulnerable versions of Flash, protecting users, and highlighting the issue at the same time. The web was full of people describing how easy it is now to live without Flash, and FaceBook’s new Chief Security Officer went so far as to call on all the browser manufacturers to get together and choose a date on which they will all disable Flash. System76, a PC maker who sell computers running Ubuntu went so far as to announce that they are abandoning Flash because it is just too dangerous.
Links:
- https://nakedsecurity.sophos.com/2015/07/14/facebooks-new-cso-comes-out-swinging-death-to-flash/
- http://www.macobserver.com/tmo/article/apple-blocks-flash-again-fixes-mac-mini-sleep-issue
- http://arstechnica.com/security/2015/07/firefox-blacklists-flash-player-due-to-unpatched-0-day-vulnerabilities/
- http://arstechnica.com/information-technology/2015/07/ubuntu-pc-maker-system76-abandons-flash-says-its-too-dangerous/
There has also been an un-related development regarding Flash’s future – it has been revealed that Adobe has been working with Google to harden Flash, making it more difficult to turn bugs into usable exploits. There have been two architectural changes made to Flash that would have neutered most of the recent flash exploits:
- (only on Chrome today, but coming to all versions of Flash later this summer) heap partitioning – storing different kinds of data in separate regions of memory provides protection against both buffer-overflow and use-after-free exploits. Both have featured in recent Flash zero-days.
- Adobe has also added protections around Vector objects, a part of Flash’s internals that has been successfully exploited in the recent past
More details: http://arstechnica.com/security/2015/07/zero-day-attacks-exploiting-flash-just-got-harder-thanks-to-new-defenses/
Political Fallout
Although not nearly as significant as the Snowden revelations, this hack gives us mere citizens a view into the kind of private-sector companies our governments are paying to do their dirty work for them (with our money!). These private companies are normally shrouded in secrecy, though they do of course publicly insist they are very ethical and would never provide services to repressive regimes or terrorists or anything like that.
We now know this private firm was selling hacking tools to all sorts of governments and groups, not just western ones, in places like Egypt, Russia, Saudi Arabia, Bahrain, the United Arab Emirates, Azerbaijan, Kazakhstan, and Uzbekistan.
We can now see how these companies pay hackers big money for zero-day exploits, which they then keep secret from the software vendors, preventing them from getting patched, and ensuring ordinary people like us are vulnerable to their dubious customers for as long as possible.
These revelations raise questions like whether it is appropriate for western governments to use tax payer money to keep citizens intentionally insecure.
It’s important to note that this company is not some kind of one-off, they are just one example of an entire secretive industry that’s providing these kinds of services to governments and other groups all around the world.
Some ‘highlights’:
- Hacking Team appear to have broken EU law and sold their tools to the Russians: http://arstechnica.com/tech-policy/2015/07/hacking-teams-surveillance-software-sold-to-kgb-successor/
- Hacking Team used BGP hack to hijack IPs they didn’t own – http://arstechnica.com/security/2015/07/hacking-team-orchestrated-brazen-bgp-hack-to-hijack-ips-it-didnt-own/
- Hacking Team say the hackers didn’t get everything, and that they still have better stuff that is still secret – http://arstechnica.com/security/2015/07/hacking-team-remains-defiant-touts-new-version-of-spyware-suite/
- Hacking Team broke Bitcoin secrecy – http://arstechnica.com/security/2015/07/hacking-team-broke-bitcoin-secrecy-by-targeting-crucial-wallet-file/
Security Light
Important Security Updates:
- Patch Tuesday has been and gone with a raft of updates from MS, Adobe, and Oracle, including fixes for Windows, Office, Flash, and Java – http://krebsonsecurity.com/2015/07/adobe-ms-oracle-push-critical-security-fixes/ (includes an Office update for Mac users: http://www.intego.com/mac-security-blog/microsoft-office-2011-14-5-3-update-patches-memory-corruption-flaws/)
Important Security News:
- Windows 10 home users will not get to control when security and features updates get installed into their OS – this is a VERY mixed bag, and really quite controversial – http://arstechnica.com/information-technology/2015/07/windows-10-updates-to-be-automatic-and-mandatory-for-home-users/
- The infamous cybercrime forum Darkode has been wrapped up by a coordinated global law enforcement takedown, resulting in 70 arrests – http://arstechnica.com/tech-policy/2015/07/criminal-hacking-bazaar-darkode-is-dismantled-and-70-members-are-busted/ (Brian Krebs gives a great rundown of Darkode’s history – http://krebsonsecurity.com/2015/07/the-darkode-cybercrime-forum-up-close/)
- The Guardian are reporting that data accidentally leaked by Google shows that 95% of ‘right to be forgotten’ requests are from ordinary members of the public looking to have their personal and private data protected, and not from criminals, politicians, or other public figures looking to hide their past misdeeds – http://www.theguardian.com/technology/2015/jul/14/google-accidentally-reveals-right-to-be-forgotten-requests
- Security researchers released work showing that theoretical attacks against RC4 are getting close to being practical. (Editorial by Bart – this is an important message for the industry – start moving away from RC4 now, it’s not gonna last, but there is nothing here for regular users to panic about at the moment) – http://arstechnica.com/security/2015/07/once-theoretical-crypto-attack-against-https-now-verges-on-practicality/
- A new bug has come to light in OpenSSL, but it’s not likely to cause much of a problem. The bug did not exist long, so it has not made it into many real-world systems, and it only affects clients, not servers, and most of our clients do not use OpenSSL – https://nakedsecurity.sophos.com/2015/07/09/the-openssl-cve-2015-1793-certificate-verification-bug-what-you-need-to-know/
- RELATED: Amazon have joined the effort to replace the behemoth that is OpenSSL with smaller, and hopefully more robust, implementations of TLS. They have released a new TLS library called s2n, and are using it in their products – https://nakedsecurity.sophos.com/2015/07/06/amazon-releases-low-cholesterol-heartbleed-medicine-s2n/
Notable Breaches:
- CVSphoto.com – http://krebsonsecurity.com/2015/07/cvs-probes-card-breach-at-online-photo-unit/
- After their spectacular breach, the director of the OPM has resigned – http://arstechnica.com/tech-policy/2015/07/opm-director-resigns-after-news-that-hack-affected-21-5-million-people/
- RELATED: A very good article by one of the many victims of the OPM breach giving a first-person perspective on this mess – http://arstechnica.com/security/2015/07/opm-got-hacked-and-all-i-got-as-a-former-federal-employee-was-a-stupid-e-mail/
- RELATED: Ars Technical have started a series on the OPM breach – http://arstechnica.com/series/feds-under-attack-opm-breach/
Suggested Reading:
- Good article explaining FireFox’s up-coming tracking protection feature – http://www.macworld.com/article/2945007/private-i-firefox-and-others-deal-with-unwanted-trackers-whether-ads-or-malicious.html
- A controversial bill is making it’s way through the US legislative process which would force social networking sites to monitor for terrorism keywords and phrases, and report users to the US government – http://www.macobserver.com/tmo/article/new-bill-could-turn-facebook-twitter-into-terrorist-watchdogs
- An interesting article on the gender discrimination in Google ad profile – https://nakedsecurity.sophos.com/2015/07/09/google-ad-profiling-whats-causing-the-gender-discrimination/
- “It’s time we stopped calling Millenials ‘dumb’ about privacy” – https://nakedsecurity.sophos.com/2015/07/08/its-time-we-stopped-calling-millennials-dumb-about-data-privacy/
Chit Chat Across the Pond
Serenity Caldwell of iMore joins us to talk Home Automation. Questions I asked Serenity include:
Can you give us a state of the union on Home Automation?
- Is there a standard yet?
- Is it too soon to get into it?
- Still time for only baby steps?
- I’ve heard about end-to-end hardware encryption – can you explain? And things WEREN’T encrypted before HomeKit?
- Queasy feeling or can be trusted?
You’re a roller derby fanatic, and been disappointed in whether you get credit for your workouts from Apple Watch, why doesn’t “other” work for that?
Plugs: http://imore.com, @settern on Twitter, settern on Instagram and The Incomparable Podcast with Jason Snell at theincomparable.com
That’s going to wind this up for this week, many thanks to our sponsor for helping to pay the bills, the makers of Clarify over at clarify-it.com. Don’t forget to send in your Dumb Questions, comments and suggestions by emailing me at [email protected], follow me on twitter @podfeet. Check out the NosillaCast Google Plus Community too – lots of fun over there! If you want to join in the fun of the live show, head on over to podfeet.com/live on Sunday nights at 5pm Pacific Time and join the friendly and enthusiastic NosillaCastaways. Thanks for listening, and stay subscribed.
