 In Dumb Question Corner, Steve’s Uncle Bob asked a really good question. It’s been a while since we did a dumb question so let’s review the rules. A Dumb Question qualifies for such a title if it’s something you feel like you should know the answer to, and figure everyone else must understand something you don’t. The questions are absolutely not dumb but it helps to call them that so you’ll feel ok asking them.
In Dumb Question Corner, Steve’s Uncle Bob asked a really good question. It’s been a while since we did a dumb question so let’s review the rules. A Dumb Question qualifies for such a title if it’s something you feel like you should know the answer to, and figure everyone else must understand something you don’t. The questions are absolutely not dumb but it helps to call them that so you’ll feel ok asking them.
The second rule of Dumb Question is that ideally Allison will be able to answer them. I’ve been known to do a bit of research from time to time to figure out the answer, but in general it’s swell if it’s actually in my field of expertise. That brings us to our third rule, and it’s that you can’t ask me anything about iTunes. With that stage sent, here’s Bob’s question:
My question revolves around whether end-to-end encrypted chat programs like WhatsApp, Signal, and others are necessary if both parties already employ VPN’s? My understanding of VPN’s is that they encrypt all data between servers and mask the original IP address. That being the case, it would seem WhatsApp and other end-to-end encryption tools would be redundant. Another question stemming from this is whether both parties have to have VPN’s on their respective ends, or will it also work if just one party uses a VPN? Just something enquiring minds need to ponder to avoid Alzheimer’s.
I like this question because I knew that all of the information to answer the question was somewhere stashed away in my brain, but retrieving the right bits and assembling them properly was going to be the tricky part.After two weeks of rolling it around, I finally assembled the answer. I ran it by Bart just in case, but I’m pleased to say that he said I got it exactly right and he didn’t change a thing. Here’s the answer to Bob’s question of whether having two people on VPNs would make end to end encryption on a messaging service unnecessary.
End-to-end encryption in a messaging service means all the way from you to me. That sounds obvious but let’s talk through how a VPN works in comparison.
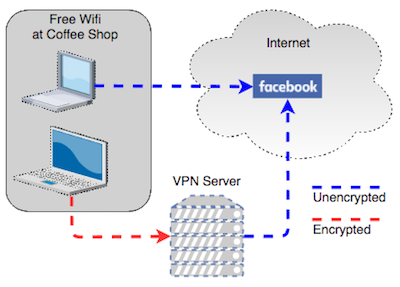
A VPN, aka Virtual Private Network, encrypts your connection from you to the VPN server, but not beyond that. So your super secret message would travel fully encrypted from you to the VPN server, but then it would travel unencrypted from the messaging server over to my VPN server. At that point it would be encrypted as it traveled the rest of the way to me. In other words, a VPN is not end-to-end.
VPNs are designed to tunnel your traffic out of wherever you are to change your starting point. Two examples of uses for this are for when you’re on an unsecured network, or if you’re in one location and want to appear to be in another location. I used TunnelBear once to pretend I was in England so I could watch women’s gymnastics during the Olympics on BBC (they weren’t broadcasting it in the US when we weren’t winning). People also use VPNs to hide themselves from scary governments and from governments which block services like Facebook.
Let’s walk through how you can look at your own traffic on a VPN, to illustrate how end-to-end isn’t part of it.
Let’s say you’re at a coffee shop that offers free WiFi. Every person in the coffee shop is on the same network as you, and you don’t know these people or whether they may have ill intent. If you engage a VPN, your network traffic travels out of the WiFi network and up to your VPN provider’s server and then from there goes to the websites and services you request.
You have essentially moved yourself to a different location before heading out to the Internet. You can prove this to yourself with an easy test. Install a VPN, say a trial of Cloak, or you could use the free version of TunnelBear. Before launching the VP, open a web browser and go to ipchicken.com. This website shows you your IP address. In my test it came back as 47.144.139.226. Now turn on the VPN and go to IP Chicken again. When I ran this test, my IP address had changed to 69.197.19.37. Clearly I have changed location.
There are websites that you can use to determine your location by IP as well. One called speedguide.net/… shows you a map given an IP address. When I put in the 69.197.19.37 address, it showed I was in Newport Beach, California, about 60 miles away from where I’m actually located. Using these VPN services you can often choose a specific country (like in my Olympics example).
Using Cloak, I told it I wanted to be in Australia. I ran IP Chicken again, and my address changed to 168.1.35.248. Using Speedguide.net again, sure enough, it says I’m in New South Wales.
The point of all this is that VPNs simply tunnel you out of wherever you are and then let you loose onto the Internet. They don’t protect your traffic from the North Koreans, the NSA, or your spouse.
I hope that answers your question, and you’ll also be interested in hearing Bart talk about the kerfuffle Into caused this week when they mistakenly reported a back door in the WhatsApp messaging service.

Steve’s Uncle Bob raised an intriguing question in the Dumb Question Corner, prompting a review of our rules. Dumb Questions are those you feel you should know but think everyone else understands better. They’re not actually dumb; calling them that encourages asking. Ideally, Allison answers these questions, with occasional research for accuracy. The third rule: no iTunes questions.
Bob asked if end-to-end encrypted chat programs like WhatsApp or Signal are necessary if both parties use VPNs. He wonders if VPNs, which encrypt data and mask IP addresses, make these tools redundant. He also asks if both parties need VPNs or if one is sufficient.
After pondering for two weeks, Allison assembled an answer, confirmed by Bart, that end-to-end encryption remains essential. While VPNs secure the data path from user to server, end-to-end encryption ensures privacy directly between users, providing an additional layer of security.